Introduction: Why BYOD Security Needs a Clear Access Model
Bring Your Own Device (BYOD)—allowing employees to access corporate systems from personal laptops, smartphones, and tablets—has become the default operating model across industries. Workforce mobility, cloud adoption, and remote work have made BYOD nearly unavoidable. Surveys consistently show that a majority of employees use personal devices for work, often without IT-issued alternatives.
The business upside is clear: flexibility, faster onboarding, and lower hardware costs. The downside is equally clear: reduced control over endpoint security, data protection, and compliance.
To manage this risk, enterprises rely on two fundamental BYOD access models:
- Agent-based access, which installs software on the endpoint
- Agentless access, which enforces security through network, identity, or cloud controls
Each model reflects a different trust philosophy, deployment burden, and risk tolerance. This article examines both approaches in depth—across MDM, NAC, IAM, and Zero Trust architectures—to help security and IT leaders make informed decisions.
Understanding BYOD and Access Models
What Is BYOD?
BYOD allows employees to use personally owned devices to access enterprise applications, networks, and data. Unlike corporate-owned endpoints, BYOD devices are:
- Not fully managed by IT
- Shared with personal applications and data
- More heterogeneous in OS versions and security posture
This makes traditional perimeter security ineffective.
BYOD Access Models at a Glance
The defining difference between BYOD security models is whether software runs on the device.
| Model | Endpoint Software | Control Plane |
|---|---|---|
| Agent-Based | Required | Device + Server |
| Agentless | Not required | Network / Identity / Cloud |
Agent-Based BYOD Access Model
How Agent-Based BYOD Works
In an agent-based model, each BYOD device installs a management or security agent. This is most commonly delivered through:
- Mobile Device Management (MDM) or Unified Endpoint Management (UEM)
- Persistent NAC or 802.1X supplicants
- Endpoint security or EDR agents
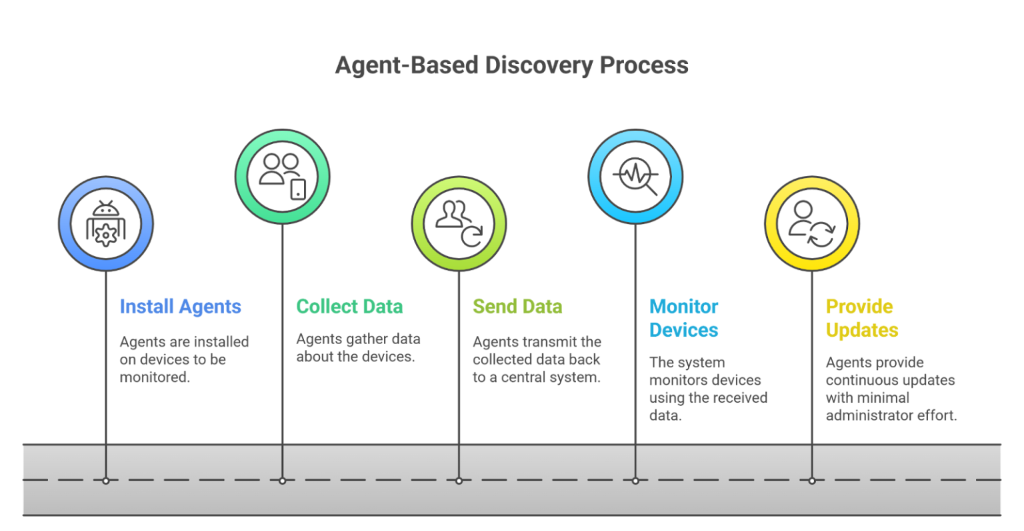
Once installed, the agent collects device telemetry (OS version, patches, apps, AV status), enforces security controls (encryption, VPN profiles, certificates), and reports posture continuously to a central console.
Because the agent runs locally, enforcement remains effective even when the device is off-network.
Advantages of Agent-Based BYOD
- Deep Visibility and Control: Agents provide granular insight into endpoint state. Security teams can enforce encryption, block jailbroken devices, control applications, and respond directly on the device.
- Continuous Monitoring (Even Off-Network): Unlike network-based checks, agents continue reporting posture regardless of location—ideal for remote and mobile users.
- Strong Compliance Alignment: Agent-based enforcement aligns well with regulated environments (PCI DSS, HIPAA, GLBA), where demonstrable endpoint controls are required.
Challenges of Agent-Based BYOD
- Deployment Overhead: Agents must be installed, updated, and supported across multiple OS platforms.
- User Privacy Concerns: Employees may view corporate software on personal devices as intrusive. Without transparency, adoption resistance is common.
- Platform Limitations: Some devices (legacy hardware, IoT, guest endpoints) cannot support agents.
Agentless BYOD Access Model
How Agentless BYOD Works
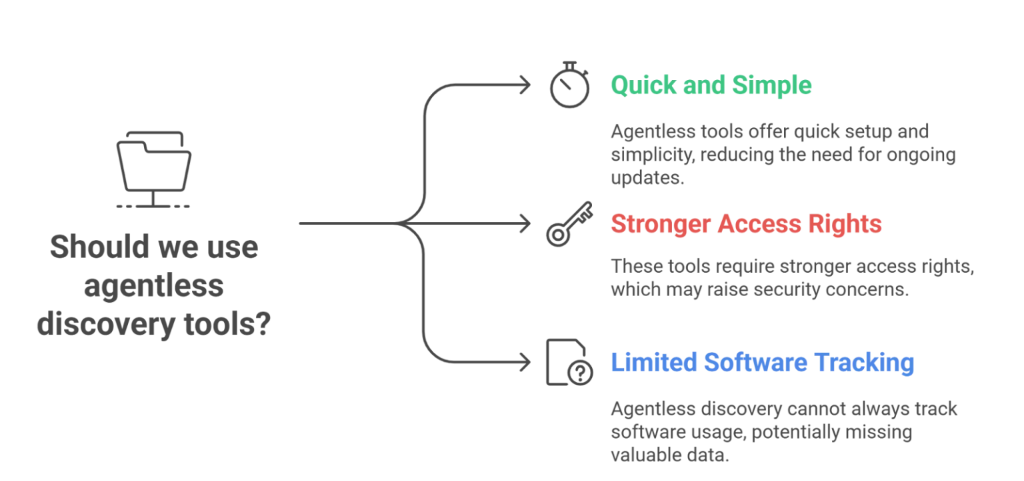
Agentless BYOD enforces security without installing software on the endpoint. Controls are applied through:
- Network Access Control (NAC)
- Identity and Access Management (IAM)
- Secure Web Gateways (SWG) and CASB
- Zero Trust Network Access (ZTNA)
Devices are authenticated and authorized at connection time using certificates, identity providers, or contextual signals.
Advantages of Agentless BYOD
- Rapid Deployment: No endpoint installation means faster onboarding and minimal user friction.
- Minimal Device Impact: No CPU, memory, or battery overhead on personal devices.
- Broad Device Compatibility: Works with virtually any endpoint, including unmanaged, legacy, or contractor devices.
Limitations of Agentless BYOD
- Reduced Posture Visibility: Without an agent, administrators lack deep insight into OS health, patch levels, or local threats.
- Connectivity Dependency: Controls typically apply only when the device is connected to known networks or cloud services.
- Infrastructure Complexity: Security logic shifts to NAC appliances, gateways, and identity platforms, increasing architectural complexity.
Agent-Based vs Agentless: Architectural Comparison
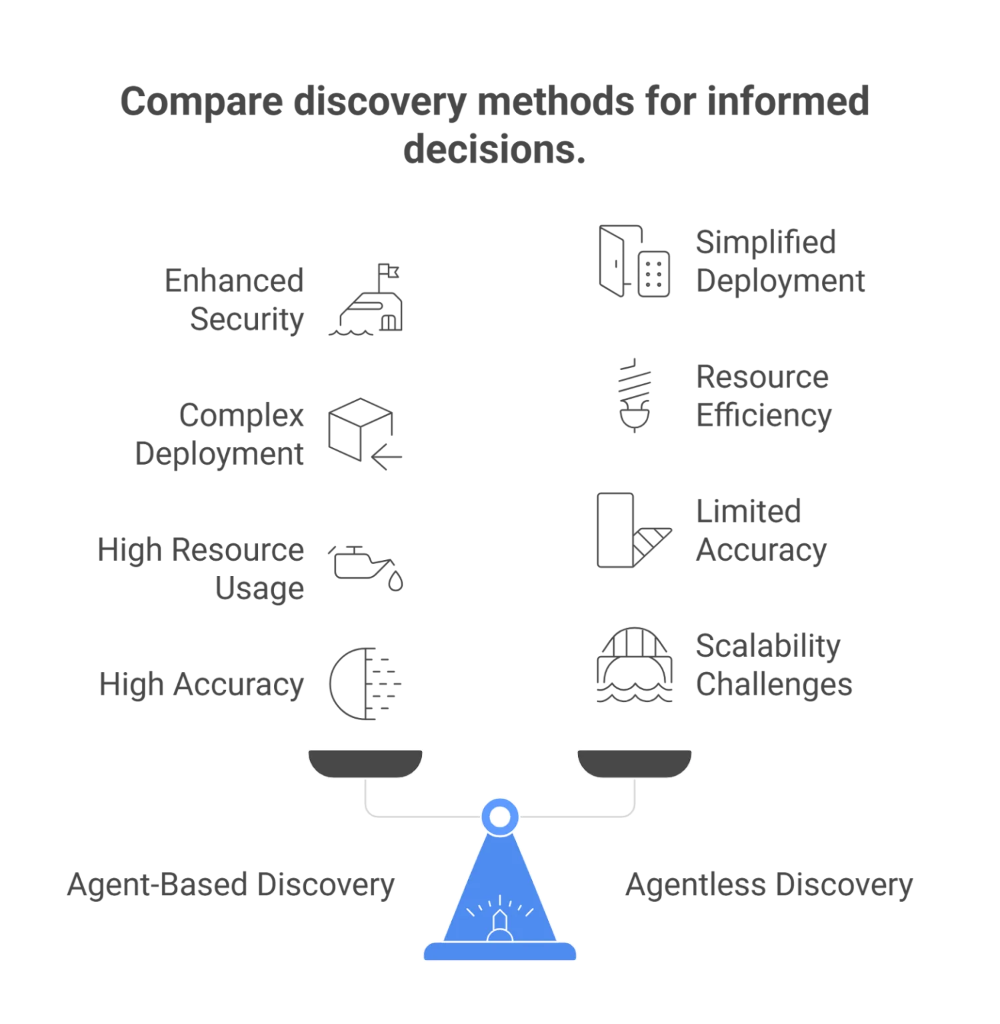
| Dimension | Agent-Based | Agentless |
|---|---|---|
| Endpoint Control | High | Limited |
| Deployment Speed | Slower | Faster |
| User Friction | Medium–High | Low |
| Visibility | Deep | Contextual |
| Compliance Readiness | Strong | Moderate |
| Device Coverage | Limited by OS | Near-universal |
Most enterprises ultimately adopt a hybrid approach.
Security Controls Across BYOD Models
MDM / UEM (Agent-Based)
MDM platforms rely on agents to enforce: Encryption, PIN / biometric policies, App containerization, and Remote wipe. They are common in highly regulated sectors.
NAC (Agent-Based and Agentless)
NAC enforces access at the network layer. Agent-based NAC uses endpoint posture agents, while agentless NAC relies on profiling, certificates, and directory signals. Many modern NAC solutions support both modes simultaneously.
Zero Trust and IAM
Zero Trust architectures—aligned with NIST guidance—evaluate user identity, device trust, and contextual risk. Identity providers such as Okta or Microsoft Entra ID enforce Conditional Access regardless of agent presence.
User Experience, Scalability, and Monitoring
User Experience: Agentless models win on simplicity. Agent-based models introduce friction but offer stronger safeguards.
Scalability: Agentless scales faster in diverse environments. Agent-based scales well once standardized but requires operational maturity.
Monitoring: Agent-based delivers real-time telemetry. Agentless relies on logs, APIs, and access events.
Compliance and Regulatory Considerations
Agent-based BYOD simplifies compliance evidence for PCI DSS, HIPAA, GLBA, SOC 2, and ISO 27001. Agentless approaches must compensate with strong access logging, network segmentation, and cloud-level DLP and encryption. In audits, regulators typically expect equivalent controls on personal and corporate devices accessing sensitive data.
Use Cases: Choosing the Right BYOD Model
- When Agentless Makes Sense: Cloud-first organizations, Contractor or guest access, Rapid onboarding requirements, Low regulatory pressure.
- When Agent-Based Is Preferred: Finance, healthcare, government, High-risk data access, Strong compliance obligations, Remote workforce with sensitive access.
- Hybrid Reality: Most enterprises deploy Agent-based controls for high-risk users and Agentless access for general staff and contractors.
Risks and Mitigation Strategies
| Risk | Primary Model Impacted | Mitigation |
|---|---|---|
| Data leakage | Agentless | CASB, DLP, encryption |
| Malware | Both | SWG, EDR, user training |
| Lost device | Agentless | Encryption, app containerization |
| Lateral movement | Both | NAC segmentation, Zero Trust |
| Shadow IT | Both | Policy, visibility, education |
Strong IAM (MFA, SSO, Conditional Access) is non-negotiable in both models.
BYOD Deployment Checklist
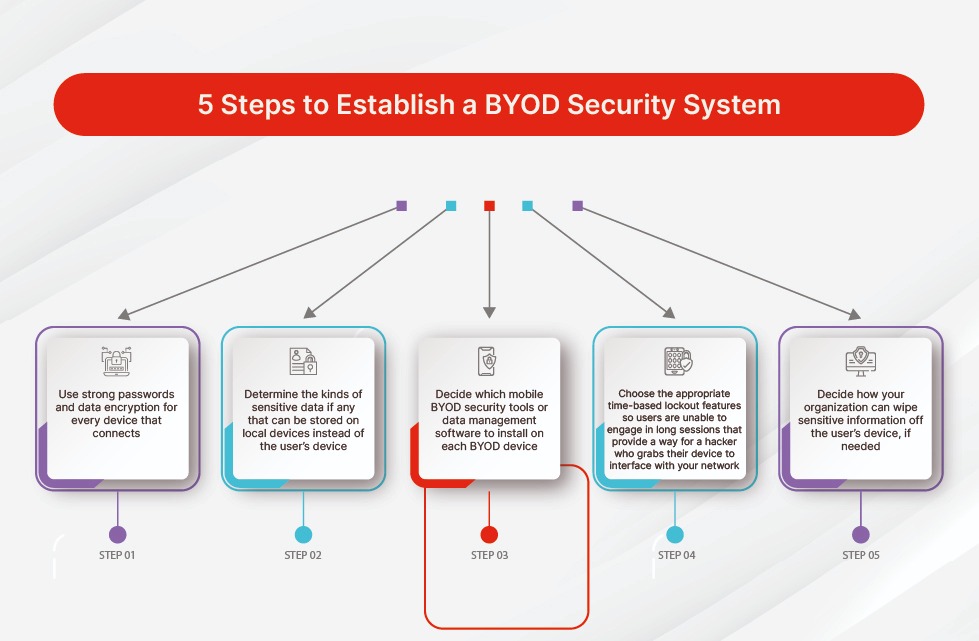
- Define and approve BYOD policy
- Classify data sensitivity
- Select agent-based, agentless, or hybrid model
- Prepare IAM, NAC, and logging infrastructure
- Run a pilot program
- Communicate clearly with users
- Roll out in phases
- Monitor, audit, and refine
Performance, Compliance, and Future Trends
Performance
Agents consume endpoint resources, whereas Agentless shifts load to network and cloud. Modern SSE platforms mitigate latency via global PoPs.
Emerging Trends
- Security Service Edge (SSE): (highlighted by Gartner)
- Risk-based Conditional Access
- Passwordless authentication (FIDO2)
- Selective, lightweight endpoint agents
The future is contextual, continuous, and adaptive.
Conclusion
Agent-based and agentless BYOD access models represent different security philosophies, not simply technical choices. Agent-based prioritizes control and compliance; agentless prioritizes usability and scale.
In practice, hybrid architectures dominate—combining identity-driven access, network enforcement, and selective endpoint agents. Organizations that explicitly choose—and document—their BYOD access model are far more resilient than those that let BYOD evolve organically.
Actionable takeaway: Define your risk tolerance, align BYOD controls with Zero Trust principles, and implement the lightest-weight controls that still satisfy security and compliance needs.