Introduction: Why Device Posture Is Now Non-Negotiable
In modern hybrid and remote-first environments, identity alone is no longer sufficient to protect enterprise systems. Credentials can be stolen, reused, or abused—but the security state of the device remains a critical line of defense.
This is where device posture assessment becomes foundational. Device posture refers to the real-time evaluation of a device’s security health—verifying whether laptops, desktops, and mobile devices meet defined security standards before accessing enterprise resources.
Zero Trust architectures explicitly depend on this concept. Zero Trust does not stop at “Who is the user?”—it also asks “Is the device they’re using secure right now?” A legitimate user accessing corporate data from an unpatched, unencrypted, or malware-infected endpoint represents a serious breach risk.
Without posture enforcement, organizations implicitly trust devices they do not control. With posture checks in place, the device itself becomes a dynamic gatekeeper, enabling stronger access control, reduced lateral movement, ransomware containment, and regulatory compliance.
Device Posture vs Device Compliance: Clearing the Confusion
Although often used interchangeably, device posture and device compliance serve different roles.
| Concept | Definition | Key Question |
|---|---|---|
| Device Posture (Descriptive) |
Represents the current security state of an endpoint (OS version, AV status, encryption, etc.). | “How secure is this device right now?” |
| Device Compliance (Evaluative) |
The policy outcome of posture assessment. It indicates whether the device meets predefined requirements. | “Does this device meet our security baseline?” |
Key distinction: Posture produces data; Compliance produces decisions.
Core Device Posture Attributes Enterprises Enforce
Most enterprise posture policies evaluate a consistent set of security attributes:
- Operating System & Patch Level: Devices must run a supported OS with current security patches applied. Unpatched systems remain one of the most common breach vectors.
- Antivirus / EDR Status: Endpoint protection must be installed, active, and up to date. Many organizations now require EDR rather than traditional signature-based AV.
- Disk Encryption: Full-disk encryption (e.g., BitLocker or FileVault) protects data at rest and is mandatory in most regulated industries.
- Firewall Status: A running, properly configured local firewall reduces exposure to network-based attacks.
- MDM / UEM Enrollment: Enrollment ensures the device is managed, visible, and enforceable under corporate policy.
- Vulnerability & Configuration Checks: Advanced posture systems validate BIOS settings, secure boot, prohibited software, and known high-risk misconfigurations.
- Additional Security Controls: These may include strong lock-screen policies, TPM or Secure Enclave presence, certificate-based authentication, and corporate application or profile installation. A single failure across these attributes is often enough to trigger non-compliance.
Agent-Based vs Agentless Posture Assessment
Organizations collect posture data using agent-based, agentless, or hybrid approaches.
Agent-Based Posture Assessment
An endpoint agent runs locally and continuously reports security data. Many NAC and EDR platforms rely on this model for corporate-owned assets.
- Strengths: Deep visibility, Real-time monitoring, Accurate vulnerability detection.
- Limitations: Requires deployment and maintenance, Less suitable for unmanaged or personal devices.
Agentless Posture Assessment
No endpoint software is installed. Posture is assessed via Identity provider signals, MDM APIs, or Network protocols (RADIUS, WMI, SSH).
- Strengths: Ideal for BYOD and guests, Minimal user friction.
- Limitations: Limited depth, Often evaluated only at access time.
Best Practice: Hybrid Coverage. Most enterprises use agents for managed devices and agentless checks for BYOD, balancing visibility with usability.
Role of Device Posture Across Security Controls
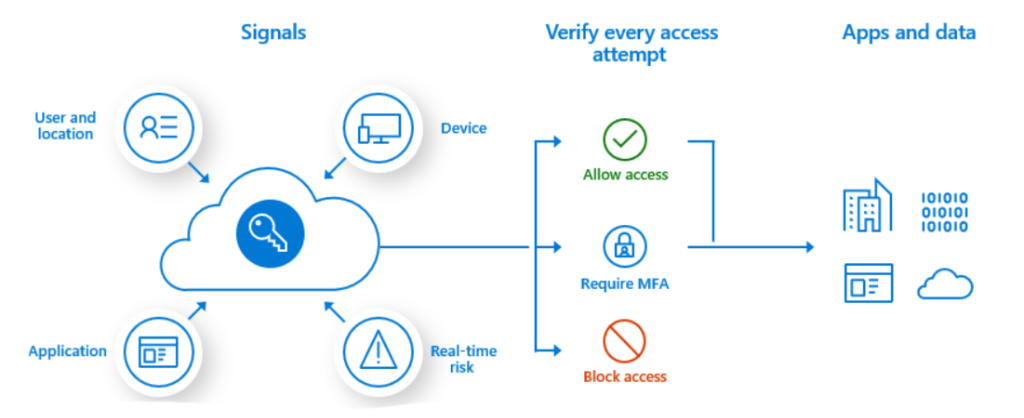
Figure 1: How device signals integrate into Zero Trust access decisions.
Zero Trust Architecture
Device posture is a core trust signal in Zero Trust. Access decisions dynamically consider:
- User identity
- Device health
- Context and risk
A compromised device can be restricted even if credentials are valid.
Network Access Control (NAC)
NAC platforms enforce posture checks at network entry points. Devices may be:
- Granted full access
- Placed in restricted VLANs
- Quarantined for remediation
NAC significantly reduces lateral movement and internal attack surfaces.
MDM / UEM Platforms
MDM tools enforce baseline security configurations and supply compliance signals to identity systems. However, without integration, MDM compliance alone does not stop access.
Conditional Access
Identity platforms enforce device compliance during authentication. Policies can require:
- Compliant devices
- MFA if non-compliant
- Restricted access for high-risk posture
Posture becomes a first-class input in access decisions.
Compliance Frameworks Supported by Device Posture
Device posture enforcement directly maps to major regulatory and industry frameworks:
- NIST (800-53, 800-171, 800-207): Patch management, malware protection, device trust
- CIS Controls: Secure configuration, vulnerability management, endpoint protection
- PCI DSS: Encryption, anti-malware, system hardening
- HIPAA: Encryption, access control, endpoint safeguards
- ISO 27001 / SOC 2 / GDPR: Asset control and data protection
Posture tools provide auditable, continuous enforcement, reducing manual compliance effort.
Common Enterprise Use Cases
- BYOD Security: Posture checks prevent unmanaged personal devices from introducing risk.
- Remote & Hybrid Workforce: Security policies follow the device—not the network perimeter.
- Audit Readiness: Real-time compliance reporting simplifies audits and due diligence.
- Ransomware & Lateral Movement Prevention: Non-compliant endpoints are automatically isolated, limiting blast radius.
- Internal Policy Enforcement: Ensures executive mandates (encryption, DLP, EDR) are actually enforced.
Challenges and Limitations
- Coverage gaps (legacy, OT, or unmanaged devices)
- Privacy concerns on personal endpoints
- Operational complexity at scale
- User friction from aggressive enforcement
- Stale posture data without continuous evaluation
These challenges argue for risk-based, adaptive enforcement, not rigid blocking.
Best Practices for Effective Posture Enforcement
- Define a clear, enforceable security baseline
- Integrate posture with identity and access systems
- Use agents where possible; agentless where necessary
- Apply Zero Trust principles (least privilege, segmentation)
- Continuously reassess posture—not just at login
- Automate remediation and user guidance
- Regularly audit coverage and policy effectiveness
- Educate users to reduce resistance and bypass attempts
Future Trends in Device Posture
- Continuous Access Evaluation (CAEP): For real-time revocation
- Risk-based posture scoring: Instead of binary compliance
- AI-driven behavioral signals: From EDR and XDR
- Cloud-native and IoT posture integration
- Unified Zero Trust platforms: Replacing siloed tools
Posture is evolving from checklist validation to continuous risk intelligence.
Conclusion
Device posture and compliance are no longer optional controls—they are core pillars of enterprise security. By validating device health in real time, organizations close a critical trust gap that identity alone cannot solve.
When integrated with Zero Trust, NAC, MDM, and Conditional Access, posture assessment:
- Reduces breach risk
- Limits lateral movement
- Simplifies compliance
- Strengthens audit readiness
Organizations that operationalize device posture as part of access control—not as an afterthought—are materially better positioned against modern threats.