Introduction: The New Network Boundary
Modern enterprise networks are no longer bounded by a physical perimeter. Employees work remotely, contractors connect intermittently, and IoT devices quietly appear on the network—often unmanaged. In this environment, the assumption that “anything inside the network is trusted” is fundamentally broken.
Network Access Control (NAC) addresses this problem by answering a deceptively simple question: Who or what is trying to connect to the network, and should it be allowed?
This article provides a deep, practical explanation of NAC for IT managers and security engineers. We’ll cover how NAC works, the role of 802.1X, deployment models, real-world use cases, benefits, challenges, myths, and best practices—so you can evaluate or design a NAC deployment with confidence.
What Is Network Access Control (NAC)?
Network Access Control (NAC) is a security framework that controls access to a network based on identity, device posture, location, and policy. It ensures that only authorized and compliant users and devices can connect—and that they receive the right level of access.
At its core, NAC enforces three principles:
- Identify – Who is the user or device?
- Evaluate – Is the device compliant and trustworthy?
- Enforce – What access should be granted (or denied)?
Unlike traditional network security tools that focus on traffic inspection after access is granted, NAC operates at the moment of connection.
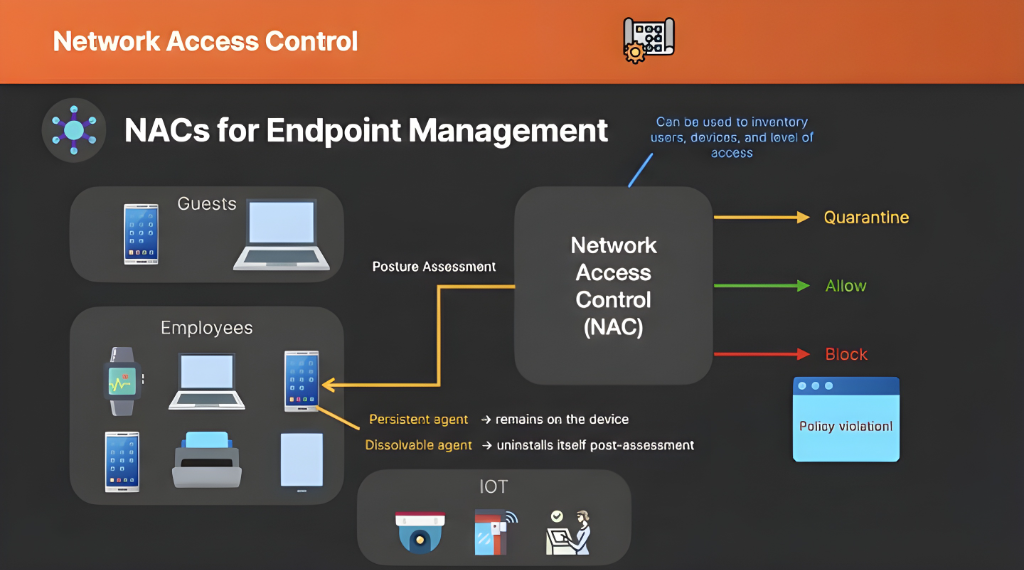
Figure 1: How NAC manages diverse endpoints (Guests, Employees, IoT) through posture assessment and policy enforcement.
Why NAC Matters in Modern Networks
Several trends have made NAC essential rather than optional:
- BYOD and remote work blur network boundaries
- IoT and OT devices lack native security controls
- Ransomware and lateral movement exploit open internal networks
- Zero Trust strategies require continuous verification
Without NAC, networks often rely on static VLANs, shared credentials, or manual approvals—approaches that do not scale and are easy to bypass.
Core Components of a NAC Solution
Most NAC solutions share a common architectural pattern, even if implementation details differ.
1. Policy Engine
The “brain” of NAC. It evaluates authentication results, posture checks, and contextual data against defined policies.
Examples of policy inputs: User identity (AD, LDAP, cloud IdP), Device type (laptop, phone, printer, camera), Security posture (AV status, OS version, patches), Location or connection method (wired, wireless, VPN).
2. Authentication Mechanisms
NAC integrates with multiple authentication methods, including:
- 802.1X (certificate- or credential-based)
- MAC Authentication Bypass (MAB)
- Web-based captive portals
- API-based identity checks
3. Enforcement Points
These are the network devices that apply NAC decisions: Switches, Wireless controllers, VPN gateways, and Firewalls (in some architectures).
4. Visibility and Profiling Engine
NAC continuously profiles devices using DHCP fingerprints, HTTP user agents, LLDP/CDP data, and traffic behavior patterns. This allows NAC to identify unmanaged or “headless” devices such as IoT sensors and printers.
How Network Access Control Works
At a high level, NAC follows a connect → evaluate → enforce → monitor lifecycle.
Step 1: Connection Attempt
A user or device connects via wired Ethernet, Wi-Fi, or VPN.
Step 2: Authentication (802.1X and Beyond)
802.1X is the gold standard for NAC authentication. It involves three roles: Supplicant (the client device), Authenticator (switch or access point), and Authentication Server (NAC or RADIUS server). If 802.1X is unavailable, NAC falls back to alternatives like MAB or device profiling.
Step 3: Posture Assessment
NAC checks whether the device meets security requirements (AV status, OS version, patches). Non-compliant devices can be redirected to remediation networks.
Step 4: Policy Decision and Enforcement
Based on identity and posture, NAC assigns VLANs, Access control lists (ACLs), Security group tags (SGTs), or Role-based access policies.
Step 5: Continuous Monitoring
NAC is not “set and forget.” It can re-evaluate posture periodically, quarantine compromised devices, and revoke access if conditions change.
NAC Deployment Models
Choosing the right NAC deployment model is critical for performance and scalability.
1. Inline NAC
Traffic flows through the NAC device. Useful for strong enforcement and full traffic visibility, but carries risk as a potential bottleneck.
2. Out-of-Band NAC (Most Common)
NAC communicates with network devices via RADIUS, SNMP, or APIs but does not sit in the traffic path. It's scalable and lower risk, matching enterprise needs.
3. Agent-Based vs Agentless
| Model | Strength | Limitation |
|---|---|---|
| Agent-Based | Deep posture checks | Requires client installation |
| Agentless | Ideal for guests & IoT | Limited posture visibility |
Common Use Cases for NAC
- Secure Enterprise Wi-Fi: Certificates for employees, captive portals for guests, and time-bound access for contractors.
- BYOD Control: Distinguishing between corporate and personal devices to assign different access privileges.
- IoT and OT Segmentation: Restricting access for devices like IP cameras and medical hardware to mandatory systems only.
- Compliance and Auditing: Providing device inventory and access logs for frameworks like ISO 27001 or SOC 2.
Network Access Control Benefits
Key benefits include reduced attack surface, stronger identity-based access, improved network visibility, automated enforcement, and faster incident response.
Challenges and Limitations of NAC
Common challenges include initial policy design complexity, legacy device compatibility, and operational overhead. NAC failures are often process failures, not technology failures.
Best Practices for NAC Deployment
- Start with visibility-only mode (Observe before enforcing).
- Segment by role, not VLAN sprawl.
- Treat IoT separately (Don't force 802.1X everywhere).
- Integrate with identity systems (AD, Cloud IdPs, MDM, SIEM).
- Plan for exceptions (Printers, legacy systems).
Common Myths About NAC
- Myth 1: “NAC is only for large enterprises” – Modern solutions scale well for mid-sized orgs.
- Myth 2: “802.1X breaks everything” – Poor planning breaks things, not the standard.
- Myth 3: “NAC replaces firewalls” – They are complementary controls.
NAC and Zero Trust: How They Align
NAC is foundational for Zero Trust, enforcing continuous verification, least-privilege access, and device trust validation. Without NAC, Zero Trust strategies often lack strong enforcement at the access layer.
Glossary of Essential Terms
- 802.1X – Port-based network access control standard
- Posture Assessment – Evaluating device security compliance
- Supplicant – Client requesting network access
- Authenticator – Network device enforcing access
- Profiling – Identifying devices based on behavior and attributes
Conclusion: Is NAC Still Relevant?
Absolutely. In a world of hybrid work and unmanaged devices, NAC remains one of the most effective ways to enforce trust before access is granted. When implemented correctly, it improves security posture without crippling operations.