Introduction: The Ongoing Debate About NAC’s Relevance
The question appears frequently in security discussions: Is NAC still relevant today?
With the rise of Zero Trust architecture, cloud-native security platforms, SASE frameworks, and advanced endpoint detection tools, some IT leaders argue that Network Access Control (NAC) has become obsolete. Others maintain that NAC is more critical than ever.
The truth is more nuanced. NAC is neither obsolete nor universally required. Its relevance depends on architecture, infrastructure footprint, risk profile, and operational maturity. However, in most enterprise environments, NAC has evolved—not disappeared.
To understand whether NAC still matters, we must examine what has changed in modern security—and what has not. As long as devices connect to networks, some form of access control remains necessary.
What NAC Was Originally Built For
Network Access Control was designed to solve a straightforward problem: prevent unauthorized devices from connecting to the network, validate user identity before granting access, and check compliance posture (patching, antivirus, configuration).
Early NAC implementations relied heavily on 802.1X authentication and static VLAN assignments. While effective in theory, these deployments were often operationally complex and disruptive to users. As a result, NAC gained a reputation for being difficult to implement and maintain. Modern solutions have addressed these hurdles, turning NAC into a key enabler for secure connectivity.
Why Some Believe NAC Is Obsolete
Several major industry shifts have contributed to the perception that NAC is outdated:
- Cloud Adoption Reduced the “Internal Network”: As organizations moved workloads to cloud platforms, traditional perimeter-based security models became less central. However, users and devices still connect somewhere—through Wi-Fi networks, VPN gateways, or hybrid environments. The network decentralized, it didn't disappear.
- Rise of Zero Trust Architecture: Many interpret Zero Trust as a replacement for NAC. But Zero Trust is a philosophy, not a product. NAC can serve as the enforcement mechanism that operationalizes Zero Trust principles at the network layer.
- Growth of Endpoint Detection & Response (EDR): If endpoints are monitored and protected, why enforce access at the network? The reality is that EDR operates on the device, while NAC operates on the network. The two address different layers of risk.
What Has Not Changed in Network Security
Despite industry evolution, certain realities remain constant and even more prominent in 2025:
- Devices still connect to networks—wired, wireless, and virtual.
- Unmanaged endpoints (BYOD, Contractors, Partners) still pose significant risks.
- IoT devices continue to proliferate and often cannot support legacy security agents.
- Compliance requirements (PCI DSS, HIPAA, SOC 2) continue to mandate strict segmentation.
- Lateral movement remains a primary attack vector used by sophisticated actors.
As long as devices connect to physical or virtual networks, some form of access control and segmentation remains necessary to prevent unauthorized lateral movement.
Where NAC Is Still Highly Relevant
1. Hybrid Enterprise Environments
In hybrid models involving corporate offices, branch locations, and remote workers, NAC provides authentication at the point of connection, role-based access control, and device posture validation. Without NAC, unmanaged devices can join internal networks without restriction, bypassing expensive perimeter controls.
2. BYOD and Guest Access
BYOD policies are widespread. NAC enables secure onboarding workflows, limited access for unmanaged devices, and network isolation for guests. Modern NAC solutions ensure that personal devices meet minimum security standards before being granted even the most limited access.
3. IoT and Operational Technology (OT)
IoT devices introduce unique challenges as they cannot install security agents. NAC provides agentless device profiling and network-based enforcement. In IoT-heavy environments like healthcare and manufacturing, NAC is often the only scalable visibility and containment mechanism available to IT teams.
4. Compliance and Regulatory Requirements
Frameworks such as ISO 27001, NIST, and PCI DSS require access control enforcement and network segmentation. NAC supports compliance posture by centralizing policy enforcement and maintaining detailed logs of access decisions, which are critical during audits.
NAC vs Zero Trust: Clarifying the Relationship
Rather than replacing NAC, Zero Trust increases the demand for enforcement layers capable of dynamic access control. As we explore in our guide on What Zero Trust Really Means, NAC can implement Zero Trust requirements by authenticating users and devices, evaluating device posture, assigning dynamic roles, and restricting lateral movement.
For a deeper dive, see our guide on How Aruba ClearPass Supports Zero Trust. In many ways, modern NAC is the "Policy Enforcement Point" that makes Zero Trust a reality on the local network.
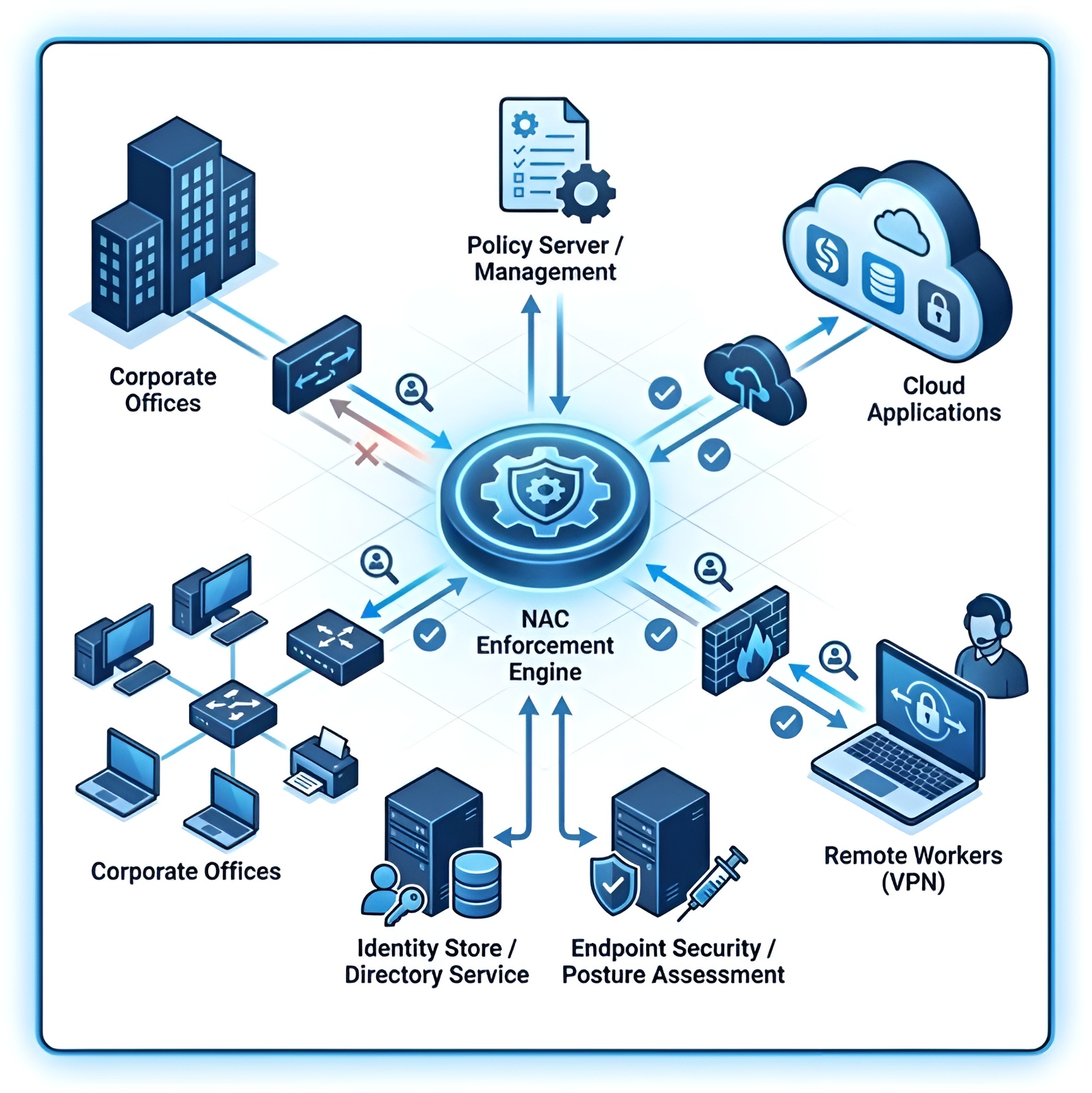
Figure 1: Modern NAC Architecture enforcing Zero Trust principles across hybrid environments.
Legacy NAC vs Modern NAC
The perception that NAC is obsolete often stems from historical experiences with legacy systems. Modern NAC platforms are architecturally distinct:
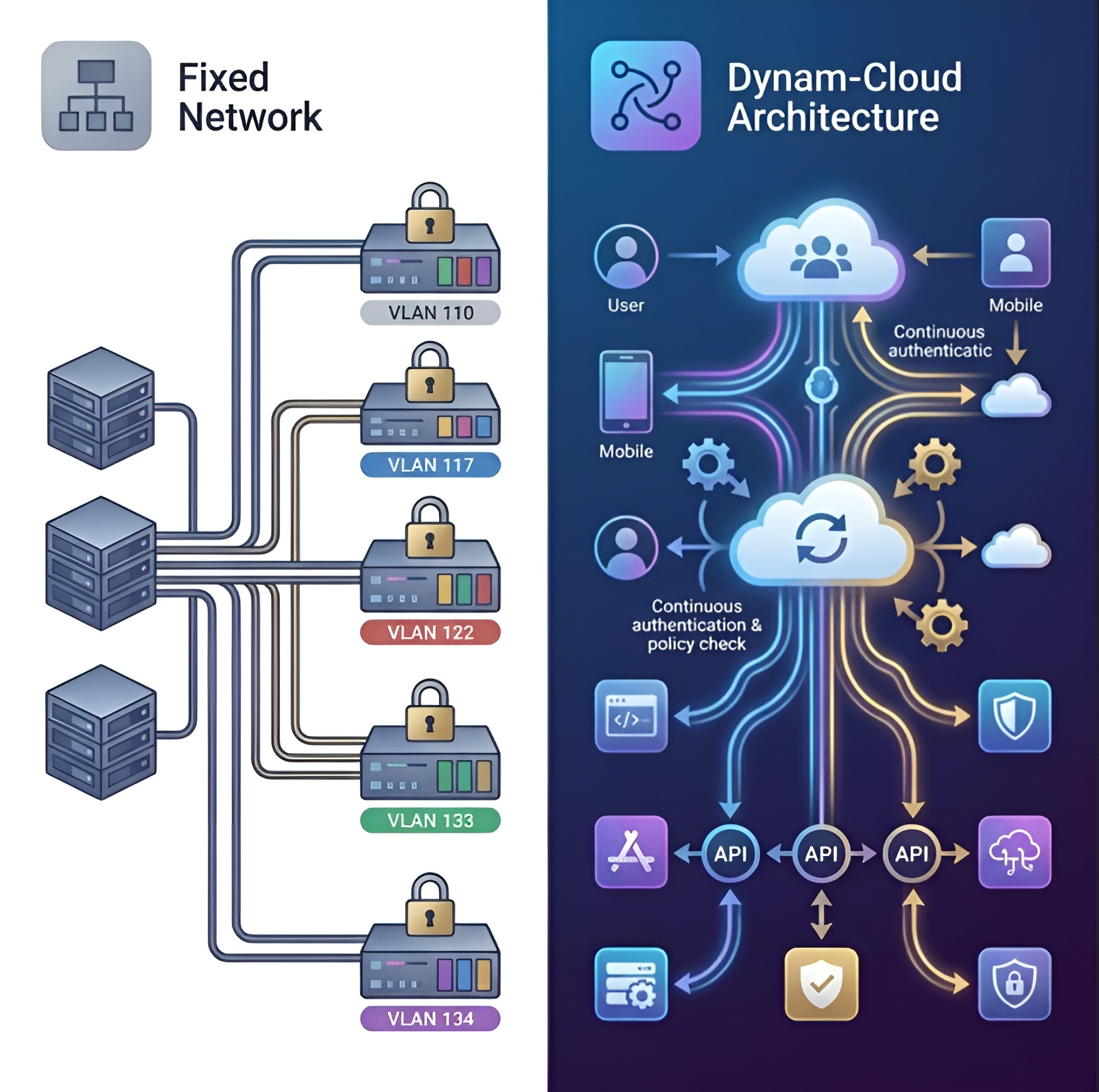
| Legacy NAC | Modern NAC |
|---|---|
| Static VLAN-based segmentation | Role-based and identity-based access control |
| Limited integration with other tools | API-driven ecosystem (SIEM/SOC/EDR/MDM) |
| Complex, rigid onboarding workflows | Cloud-managed, seamless user experience |
| Internal-only focus | Hybrid, multi-cloud, and remote enforcement |
Final Verdict: Is NAC Still Relevant Today?
Yes—for most enterprise environments, NAC remains relevant and often essential.
NAC is most valuable when it integrates with identity platforms, enforces least privilege dynamically, supports device posture checks, and aligns with Zero Trust principles. Organizations that modernize their NAC approach gain improved security posture, better compliance readiness, and greater operational visibility.
The real question is not whether NAC is relevant. It is whether your environment still contains networks, unmanaged devices, and segmentation requirements. For most enterprises, the answer is a resounding yes. If you are still relying on static network security, it may be time to evaluate how modern NAC best practices can transform your security strategy.