Introduction: Cutting Through the Zero Trust Hype
Zero Trust has become one of the most widely used—and misunderstood—terms in cybersecurity. It appears in vendor presentations, product datasheets, and boardroom discussions. Yet in many cases, what is labeled “Zero Trust” is simply traditional security with updated terminology.
So what does Zero Trust really mean, beyond marketing?
This article explains the core principles of Zero Trust security, how it works in practice, what it is not, and how organizations can implement it realistically in today’s distributed enterprise environments.
Zero Trust: The Core Principle
At its foundation, Zero Trust is built on one simple assumption: Never trust by default. Always verify explicitly.
The fundamental shift from perimeter-based trust to continuous verification.
Traditional security models assumed that users and devices inside the corporate network could be trusted. Once authenticated and connected, they were often granted broad access. Zero Trust rejects that assumption. It treats every request—internal or external—as potentially risky and requires verification before granting access.
This does not mean “trust no one.” It means “trust must be continuously earned.”
Why Zero Trust Emerged
Zero Trust became necessary because traditional perimeter-based security models broke down. Three major shifts accelerated its adoption:
- Cloud computing: Applications moved outside corporate data centers to SaaS and IaaS providers.
- Remote work: Employees now connect from home, coffee shops, and travel destinations.
- Device diversity: BYOD and IoT expanded the attack surface beyond manageable corporate laptops.
When users, applications, and devices operate across distributed environments, the idea of a single trusted internal network no longer applies. Zero Trust adapts to this reality.
What Zero Trust Is Not
Before defining what Zero Trust is, it helps to clarify what it is not:
- It is not a single product or license.
- It is not just Multi-Factor Authentication (MFA).
- It is not a firewall upgrade.
- It is not a marketing label you attach to existing tools.
Zero Trust is an **architectural strategy** that coordinates identity, device health, access control, and monitoring into a unified, resilient model.
The Three Core Principles of Zero Trust
Although implementations vary, most industry frameworks (like NIST SP 800-207) share three foundational principles:
1. Verify Explicitly
Every access request must be authenticated and evaluated using multiple signals, such as user identity, device posture, location, risk level, and time-based context. Access decisions should be data-driven rather than assumption-based.
2. Enforce Least Privilege
Users and devices receive only the minimum access required to perform their tasks. This reduces lateral movement and limits the blast radius of security incidents. Least privilege should apply to network access, application access, and administrative rights.
3. Assume Breach
Zero Trust operates under the assumption that compromise is possible—or already occurring. This mindset drives continuous monitoring, microsegmentation, and rapid detection. Rather than focusing solely on prevention, Zero Trust emphasizes resilience and containment.
How Zero Trust Works in Practice
Zero Trust implementation involves multiple coordinated components working in sync:
.png)
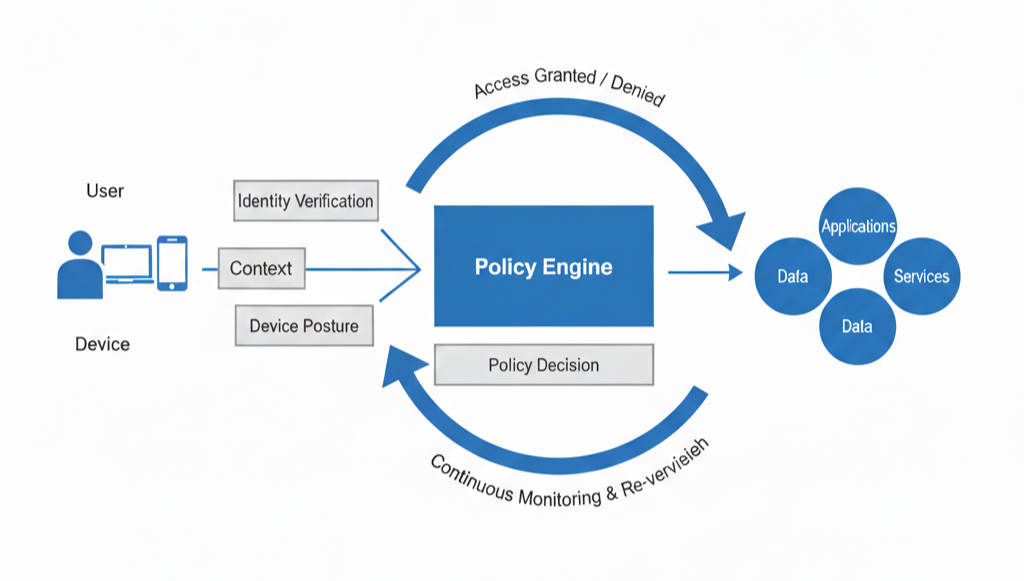
Figure 2: The logical flow of a Zero Trust access request, from identity check to continuous authorization.
Identity Verification & Device Validation
Identity is the new perimeter. Every user must authenticate using strong identity controls (MFA). Simultaneously, devices are evaluated before granting access. This includes checking OS patch levels, encryption status, and EDR health signals. If a device does not meet the policy requirements, access is restricted. This process is a core part of modern NAC implementation strategy.
Continuous Authorization & Microsegmentation
Authorization decisions are not static. Even after initial access is granted, policies can be re-evaluated dynamically. If risk changes—such as suspicious behavior—access can be revoked immediately. Furthermore, microsegmentation isolates workloads and users, preventing attackers from moving laterally across systems.
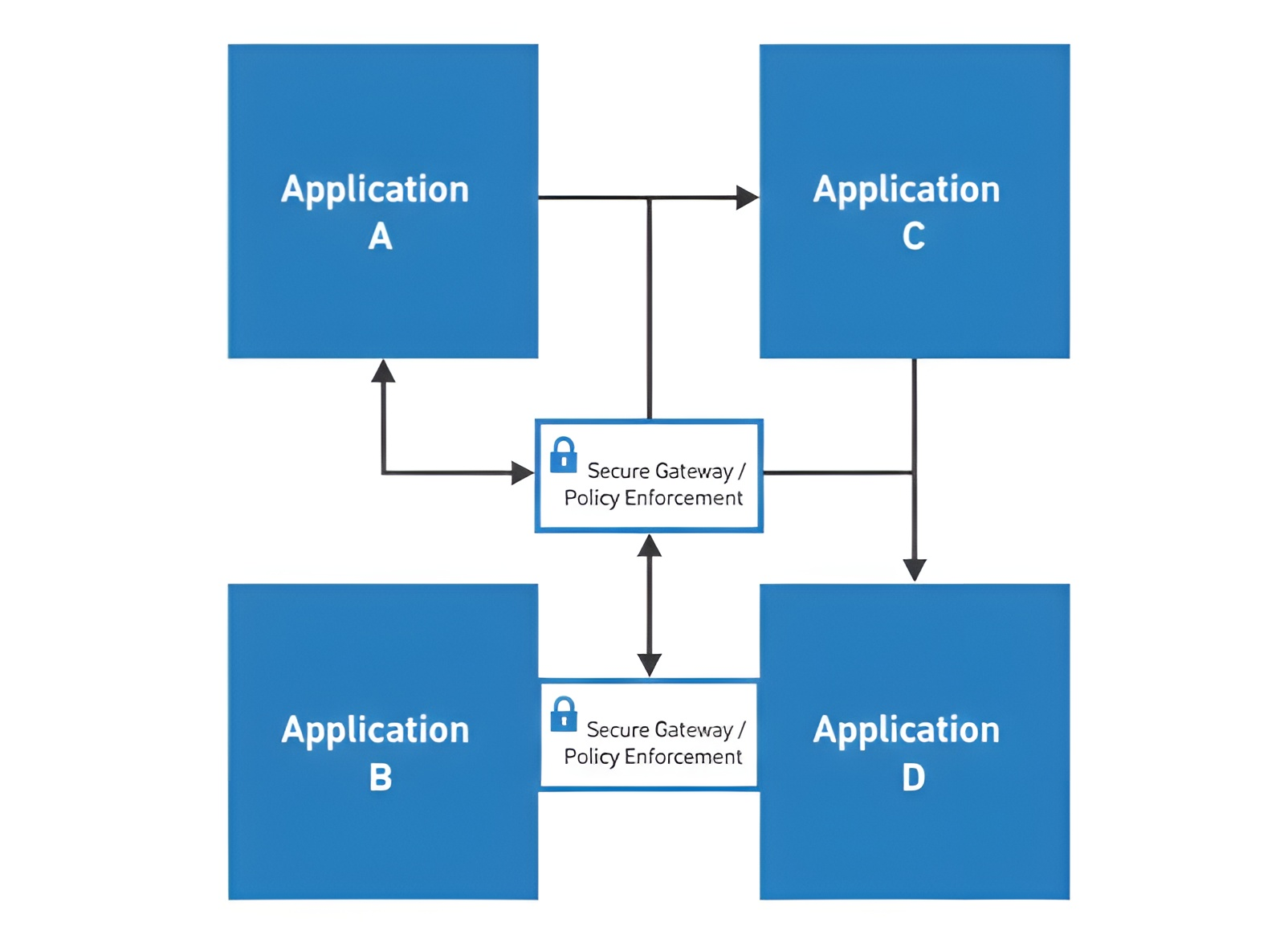
Zero Trust and Network Access Control (NAC)
While Zero Trust is often associated with cloud platforms, network-level enforcement remains critical. In environments with physical offices, branch locations, or IoT devices, Network Access Control (NAC) serves as the policy enforcement point for device authentication and compliance posture validation. Zero Trust defines the principles; NAC provides the enforcement layer.
Zero Trust vs Traditional Security Models
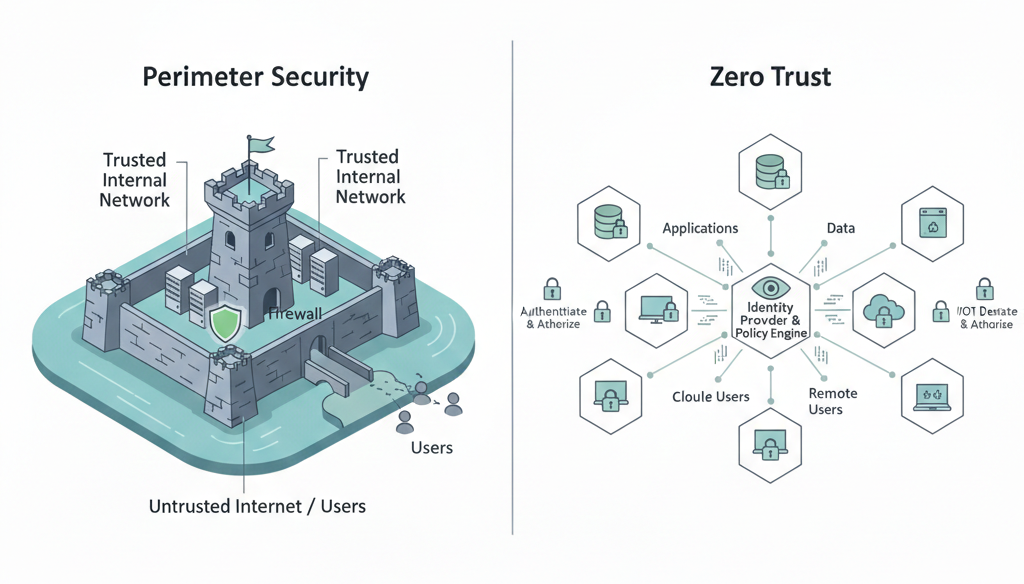
| Traditional Model | Zero Trust Model |
|---|---|
| Trust internal network | Trust nothing by default |
| Perimeter-based defense | Identity and context-based defense |
| Static access control | Dynamic, policy-driven access |
| Broad permissions | Least privilege (micro-segmentation) |
| Implicit trust after login | Continuous verification |
A Practical Approach to the Zero Trust Journey
Organizations should avoid trying to “do Zero Trust” all at once. A phased approach is more sustainable:
- Inventory: Catalog all users, devices, and applications.
- Identity: Strengthen authentication with MFA and SSO.
- Segmentation: Start with critical workloads and high-risk segments.
- Visibility: Improve monitoring and behavioral analytics.
Conclusion: Beyond the Marketing
Zero Trust is not a checkbox. It is a disciplined approach to security that recognizes three realities: the perimeter is gone, identity alone is insufficient, and trust must be continuously evaluated. When implemented thoughtfully, Zero Trust transforms security from static defense to dynamic risk management.