Network Access Control (NAC) is often positioned as a foundational control in modern enterprise security. It promises visibility into connected devices, enforcement of compliance posture, dynamic segmentation, and alignment with Zero Trust principles.
Yet despite these benefits, NAC deployments frequently stall, underperform, or fail outright.
The failure is rarely about the technology itself. More often, NAC deployments fail due to planning gaps, unrealistic expectations, weak integration strategy, or operational misalignment.
Understanding why NAC deployments fail is critical for organizations planning to implement or modernize NAC solutions. When approached strategically, NAC can deliver measurable improvements in security posture and risk reduction. When rushed or poorly governed, it can disrupt operations and erode executive confidence.
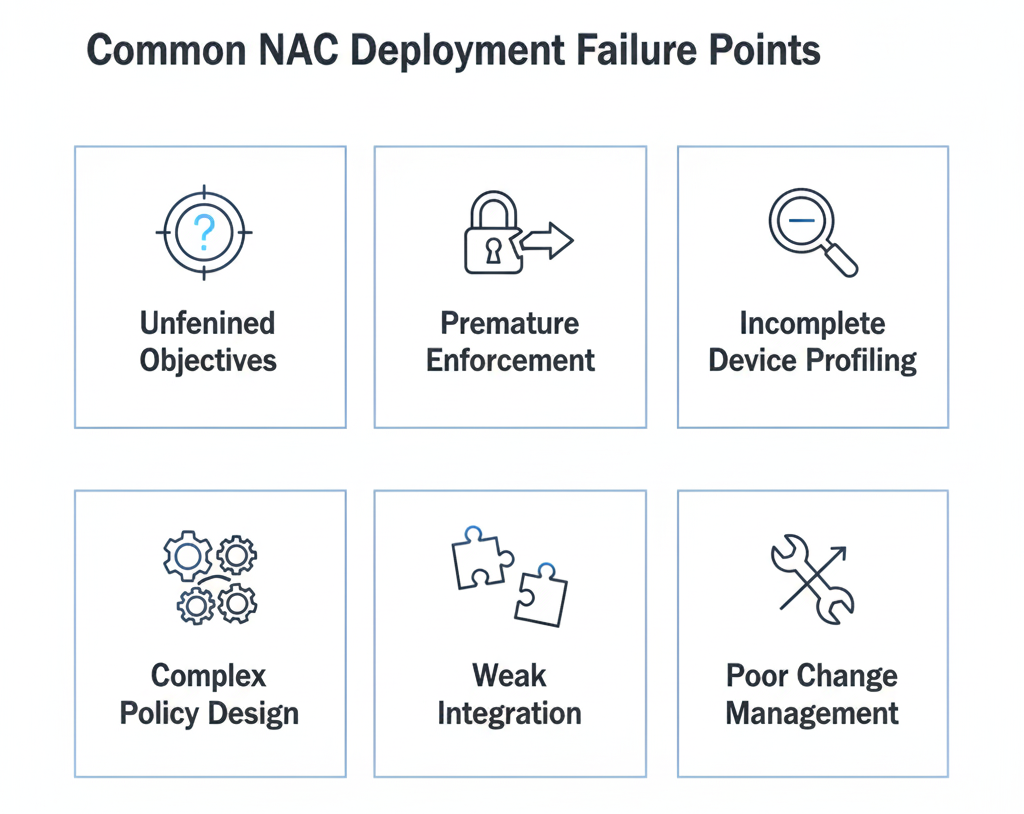
Infographic: Summary of the most frequent technical and operational NAC failure points.
The Nature of NAC: High Impact, High Sensitivity
Unlike many security tools that operate passively, NAC directly controls connectivity. It determines:
- Who can access the network
- What devices are permitted
- Whether compliance posture requirements are met
- How segmentation is enforced
Because NAC sits in the access path, misconfigurations can immediately impact business operations. This operational sensitivity is one of the primary reasons deployments require disciplined execution.
1. Lack of Clear Business Objectives
One of the most common causes of NAC deployment failure is starting without clearly defined objectives.
Organizations often launch NAC projects with vague intentions such as:
- “Improve security posture”
- “Enable Zero Trust”
- “Meet compliance requirements”
These goals are directionally correct but operationally insufficient.
A successful NAC deployment requires defined outcomes, such as:
- Reduce unmanaged devices by X%
- Enforce device posture checks before full network access
- Segment IoT devices from corporate systems
- Support specific regulatory requirements
Without measurable objectives, policy design becomes inconsistent and overly complex.
2. Treating NAC as a One-Time Project
NAC is not a one-time implementation. It is an ongoing program. Deployments fail when organizations:
- Complete configuration
- Enable enforcement
- Consider the project finished
Modern networks are dynamic. Devices change, firmware updates occur, roles shift, and new applications are introduced. NAC policies must evolve continuously. Without assigned operational ownership, NAC environments gradually degrade into overly permissive or brittle configurations.
3. Premature Enforcement
One of the fastest ways to derail a NAC project is enabling full enforcement too early.
Common symptoms of premature enforcement include:
- Users being locked out unexpectedly
- Printers and IoT devices disconnected
- Executive access interrupted
- Emergency policy rollbacks
Best practice dictates beginning with visibility or monitor-only mode. Profiling should be validated, posture checks tested, and remediation workflows documented before enforcement expands. Skipping this phase often results in reputational damage that is difficult to recover from. (Refer to our NAC best practices for more details).
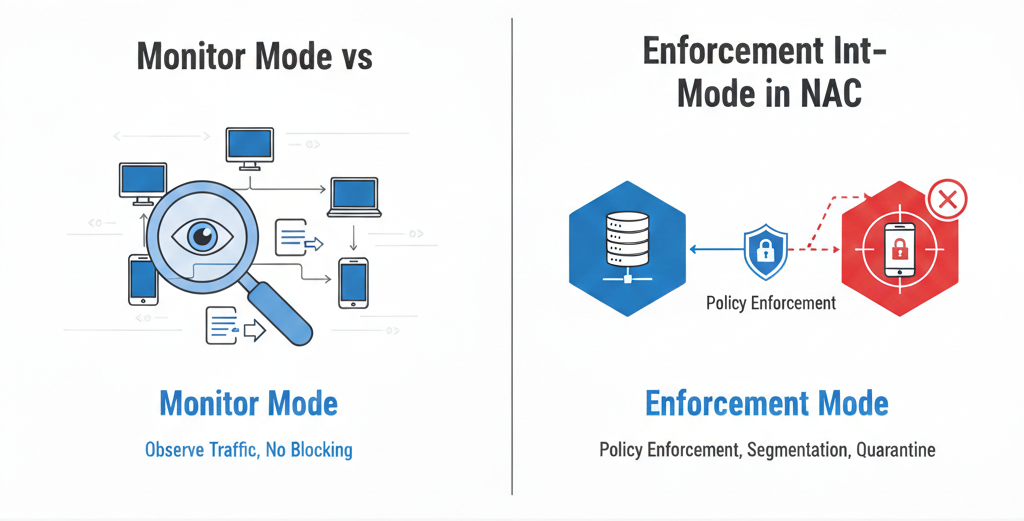
Monitor Mode vs. Enforcement: The critical bridge to a successful rollout.
4. Incomplete Device Profiling
Modern enterprise networks include:
- Corporate-managed endpoints
- BYOD devices
- Guest devices
- IoT endpoints
- Operational technology systems
- Legacy infrastructure
If profiling mechanisms are not tuned properly, devices may be misclassified. This leads to:
- Incorrect VLAN placement
- Inappropriate policy enforcement
- Disruption of business-critical systems
Accurate profiling is foundational to successful NAC enforcement. Many failed deployments underestimate this complexity.
5. Overly Complex Policy Design
Complexity is another common failure driver. Symptoms include:
- Excessive VLAN segmentation
- Hundreds of granular roles without business alignment
- Redundant or conflicting authorization rules
- Poor documentation of policy logic
Complex policies increase troubleshooting time and create operational friction. NAC designs should align to business functions rather than technical granularity alone. Clear, role-based segmentation is more sustainable than fragmented micro-policy structures.
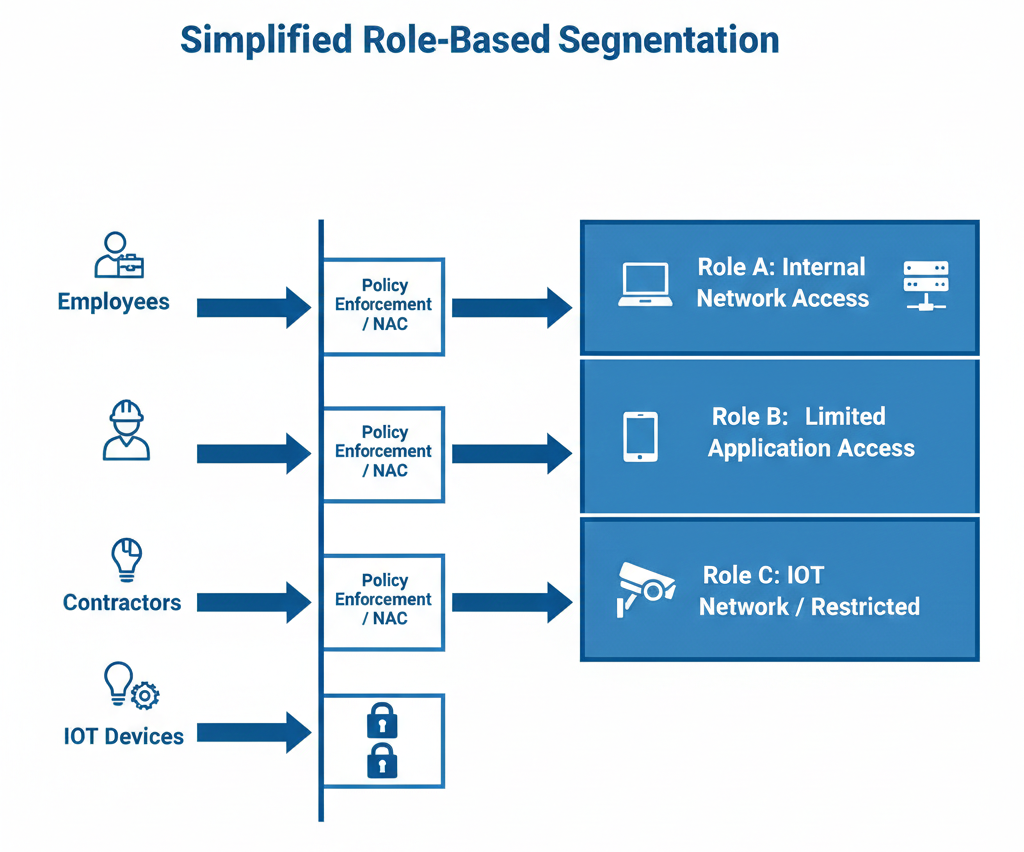
6. Weak Integration Strategy
NAC rarely operates independently. It typically integrates with:
- Identity providers (Active Directory, Azure AD, LDAP)
- Endpoint detection and response (EDR) tools
- Mobile device management (MDM) platforms
- SIEM systems
- Network infrastructure (switches, wireless controllers, VPN gateways)
Failures often stem from:
- Inconsistent identity attributes
- Unreliable posture signals
- Incomplete RADIUS configuration
- Logging gaps
Integration planning must be validated before large-scale enforcement begins. NAC effectiveness depends heavily on ecosystem alignment. (See our guide on ClearPass misconfigurations).
7. Underestimating Organizational Impact
NAC impacts multiple internal teams:
- Network engineering
- Security operations
- Helpdesk
- Infrastructure teams
- End users
Deployments fail when these groups are not aligned. Common friction points include:
- Helpdesk overwhelmed with access tickets
- Network engineers bypassing enforcement for expediency
- Security teams pushing stricter policies without operational input
- Executives reacting negatively to user disruption
Cross-functional coordination is not optional—it is essential.
8. Poor Change Management
Because NAC directly affects connectivity, communication is critical. Failures often involve:
- No user education on authentication changes
- Lack of documentation for BYOD onboarding
- Unclear remediation guidance
- No pilot phase
Effective change management should include:
- Controlled pilot deployments
- Clear communication campaigns
- Defined escalation paths
- Structured rollout phases
Ignoring user experience considerations frequently results in resistance and rollback.
9. Legacy Systems and Unsupported Devices
Legacy systems present a major deployment risk. Older devices may lack support for:
- 802.1X authentication
- Modern encryption standards
- Current firmware requirements
If these devices are not identified early, they may be disconnected during enforcement. Successful NAC strategies include:
- Dedicated exception policies
- Segmented legacy networks
- Documented risk acceptance decisions
Failure to account for legacy constraints often leads to outages.
10. Unrealistic Executive Expectations
Some organizations expect NAC to deliver immediate, transformative security improvements. However, NAC:
- Does not eliminate endpoint risk
- Does not replace EDR solutions
- Does not automatically achieve Zero Trust maturity
- Does not guarantee breach prevention
NAC strengthens network-level access control and segmentation. It must operate alongside identity, endpoint, and monitoring controls. Misaligned expectations can lead leadership to misinterpret implementation challenges as failure.
11. Misalignment with Zero Trust Strategy
Modern security initiatives often revolve around Zero Trust principles:
- Continuous verification
- Least privilege access
- Context-aware authorization
If NAC is deployed as static VLAN enforcement rather than dynamic policy enforcement, it appears outdated and disconnected from broader strategy. Successful deployments align NAC with identity-driven, posture-aware decision logic.
12. Lack of Continuous Monitoring and Optimization
Even well-executed NAC deployments can fail over time if monitoring declines. Indicators of degradation include:
- Frequent manual bypasses
- Disabled posture checks
- Increasing exception policies
- Stagnant segmentation models
Continuous monitoring and periodic review are necessary to maintain effectiveness.
Signs a NAC Deployment Is at Risk
Warning indicators include:
- High user lockout rates
- Emergency rollbacks during rollout
- Escalating helpdesk tickets
- Security teams bypassing enforcement
- Executive dissatisfaction
- Inaccurate device visibility reports
Recognizing these early allows corrective action before trust is lost.
How to Prevent NAC Deployment Failure
Organizations can improve success rates by adopting structured governance:
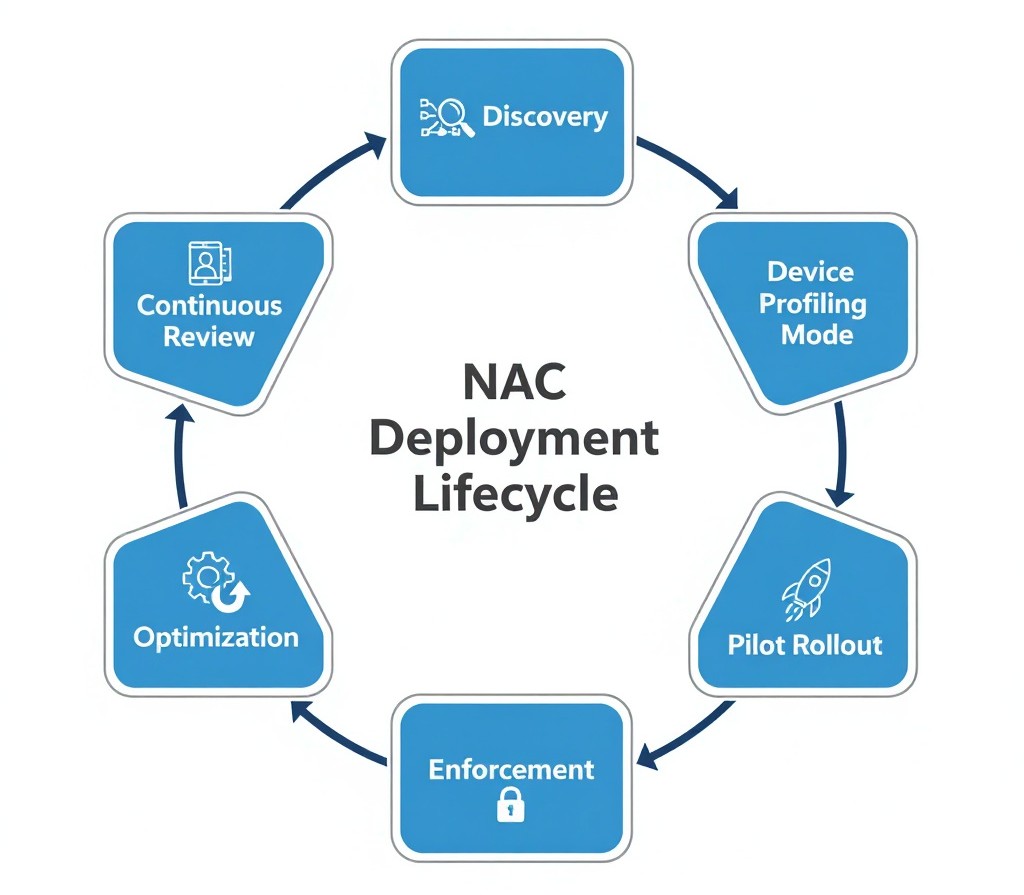
- Define measurable objectives tied to business risk.
- Begin with visibility mode before enforcement.
- Profile devices comprehensively.
- Design simple, business-aligned policies.
- Validate integrations thoroughly.
- Roll out in controlled phases.
- Assign long-term operational ownership.
- Align NAC strategy with Zero Trust architecture.
When executed deliberately, NAC strengthens network-level enforcement and reduces lateral movement risk.
Final Perspective
NAC deployments do not fail because Network Access Control is obsolete or ineffective. They fail because NAC directly influences network access, making it both powerful and sensitive.
Organizations that approach NAC as a strategic security program—rather than a technical checkbox—are far more likely to achieve sustainable success.
The lesson is not to avoid NAC. The lesson is to deploy it with discipline, governance, and realistic expectations. (For expert assistance, check our NAC Deployment Services).